by Nimal Gunarathna, P.Eng. CISSP,CISA,CCSK,CRISC,PMP,CISM,GICSP,CDPSE

Passwords have been the chief means of secure authentication for decades, but it’s now widely understood that they are no longer enough. It is too easy for cybercriminals to guess, crack, or intercept passwords using freely available hacking tools. The statistics speak for themselves; passwords alone cannot adequately protect systems against cybercrime.
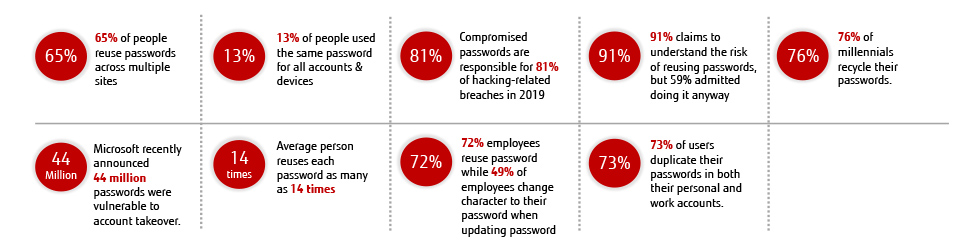
(Sources are cited at the end of this blog.)
Various Password Cracking Techniques Make Life Easier for Cybercriminals
Cybercriminals are using various techniques to crack passwords. And based on the above statistics, they don’t have to spend much time or effort to get your password. Below is a list of hacker-popular ways to crack passwords.
Phishing – The most common technique used by hackers, phishing is a type of social engineering attack that involves camouflaging malicious content within apparently trustworthy communication, such as email. The goal is to employ deception to obtain sensitive personal information such as access credentials, credit card numbers, or financial data. While the most common medium for phishing is email, text messages are also used and known as “smishing” (SMS phishing).
Social Engineering – Another easy hacking method, social engineering describes techniques for simply tricking or manipulating a user into believing the hacker is a legitimate agent. It is common for the criminal to call the victim and pose as technical support, an employee of the victim’s bank, or even a government or law enforcement agency and use this trickery to obtain all manner of sensitive information, including access credentials.
Malware – Various malicious software tools, such as key loggers and screen scrapers, can be covertly activated to steal sensitive data. Malware and malware links can be embedded into an email, text message, file attachment or downloadable files from websites.
Brute-Force Attacks – Cybercriminals can deploy malicious security tools that cycle rapidly through many character, number, and symbol permutations to uncover passwords.
Dictionary Attacks – Dictionary attacks are a common variant of brute-force techniques, in which an attacker uses a large, but defined, set of likely combinations to guess passwords. Hackers may try commonly used words such as sport teams, pet names, common family or given names, or employer-based vocabulary, such as product names.
Rainbow Table Attacks – A rainbow table is a set of precomputed hash values that represent password combinations can be used in password attack processes. This approach usually produces results more quickly than dictionary attacks.
Massive Security Breaches Underscore the Need for Better Protection
These are just a few well-known examples. Many other techniques and tools exist to help imposters crack passwords, but the important point to remember is that even a very complex password provides no guarantees. An impostor can almost certainly obtain any password through social engineering techniques and/or hacking tools. One famous attack was a 2013 data breach where hackers used a large-scale social engineering attack to access over 40 million Target customers’ credit and debit card information. These criminals sent out phishing emails to Target’s HVAC vendor Fazio Mechanical Services (FMS). Target had given remote access to FMS, and criminals plotted their attack path through FMS.
What is the Best Way to Make Authentication Safe?
So how can we make authentication stronger and more secure? How do you really prove you are you? In the real world, we have hard-to-forge physical proof of identity available, such as driver’s licenses, passports, and other photo identity cards that enable identity to be quickly verified by comparing the ID with the real person. But when you are attempting to access a computer system remotely, passwords may provide a good first layer of protection, but since attackers can guess or intercept them with increasing ease, additional security measures are required to reinforce passwords in case an attacker does obtain them.
It should be well understood by now that you can strengthen password protection to a degree by avoiding passwords based on personal information; using the longest password or passphrase possible (8–64 characters); and by not sharing your passwords with anyone else. But true identity assurance is a fundamental requirement of any robust security environment. Security is not just about having the best locks in the world; it is also about knowing who has the keys and ensuring that they are the only people who can use them. So, back to the question: How do you prove you are you to a computer system in the online world, as opposed to a person in the physical world? Thankfully, Multi-Factor Authentication (MFA) can help in a variety of ways.
Multi-Factor Authentication to the Rescue
MFA is a method of authorizing a user’s claimed identity and granting that user access to a system by requiring additional identifying factors, often based on unique physical characteristics. An example might be something the user knows, has, or is; MFA factors can be derived from any of the three. Examples include temporary access codes sent to a user’s phone; links provided via email; biometrics such as a finger or thumbprint; voice recognition; and even retinal scanning.
Fujitsu addresses MFA through its Biometrics-as-a-Service solution, which is a massively scalable, globally available solution that will quickly assist organizations with determining an identity in the first instance, via identification, or by verifying against a known identity, (i.e. authentication).
With over 20 years’ experience in biometrics, Fujitsu has the capability and solutions to help customers understand and solve their biometric needs and options. With experience in virtually all biometric and identity verification domains, Fujitsu can demonstrate how the Biometrics-as-a-Service solution can quickly deliver identity assurance, i.e. providing complete trust in “who” is using the system, in each specific problem space.
Fujitsu Solution
Fujitsu’s Cloud-based Biometrics-as-a-Service (BIOaaS) solution is a massively scalable, multi-modal secure solution capable of functioning in a variety of ways.
- Complete Identity Management-as-a-Service – Securely stores all biometric and biographic information in the cloud.
- Anonymous Biometrics-as-a-Service – No personally identifiable information (PII) leaves the organization.
- Anonymous Biometrics matching service – All information is stored in house and only the specific biometric templates being matched are sent to the cloud.
Mobile Device Capabilities
Identity security does not have to be confined to the desktop. The BIOaaS solution can use and match against biometrics data collected via traditional means, as well as utilizing the existing capabilities of today’s smartphones and tablets. This gives enterprises the flexibility to quickly and easily extend any corporate or customer identification scheme to:
- Provide in-band mobile verification
- Require users to use biometrics to verify identity to log in to various systems and functions via phone or tablet apps
- Provide out-of-band mobile verification
(“Out-of-band” means using a different access channel to verify identity. With the use of secure push notification, a user can be verified via their registered mobile device, “out of band” of traditional transactions, i.e. in-person or online transactions. This means that all types of customer interaction can be secured to the same trust level, so that criminals cannot shift attacks to less secure access channels.)
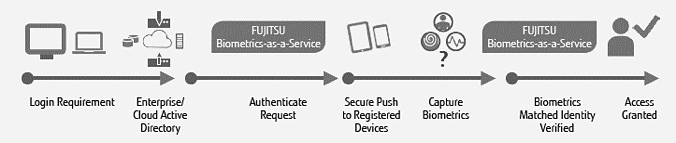
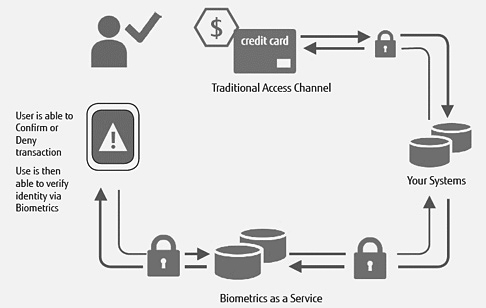
An Enterprise-Ready, Massively Scalable Biometric Multi-Factor Authentication Solution
The Fujitsu BIOaaS solution is enterprise ready, massively scalable, utilize your existing hardware such as smart phones, no up-front cost, pay as you go and ultra-scalable innovative technology solution. For more information or for a live demo request, please contact nimal.gunarathna@fujitsu.com
Sources
65% – Security Boulevard
91% – Security Boulevard
44 million – Security Boulevard & Microsoft/Forbes
14 times – Security Boulevard
72% – Security Boulevard
73% – Security Boulevard
13% – WeLiveSecurity
81% – IDagent