
Addressing 5G security concerns in Open RAN
Previously, a few major vendors wielded a lot of control over the Radio Access Network (RAN) market. However, the introduction of Open RAN has allowed operators to choose from multiple vendors and has disrupted the market for RAN implementations. These vendors are now trying to downplay the benefits of Open RAN and are focusing on the issue of cybersecurity in order to maintain their market dominance. It’s important to remember that cybersecurity is important for business success, and as long as efforts to improve 5G security in Open RAN are economically viable and lead to business advantages, the technology will thrive.
Open RAN, or Open Radio Access Network, refers to a type of telecommunications network architecture that is designed to have open interfaces and be interoperable. This is in contrast to traditional, proprietary network architectures that are closed, and which rely on a single vendor to provide all of the hardware and software components. Open RAN is also seen as a technological revolution, not as an evolution, as it represents a significant shift away from the traditional, proprietary network architectures that have dominated the telecommunications industry for decades. The security of Open RAN (radio access network) versus Closed RAN is a topic of a discussion in the telecommunications industry and various governments around the world as it is highlighted by those vendors from all directions. The diagram below from the Cybersecurity & Infrastructure Security Agency (CISA) gives an overview of Open architecture.
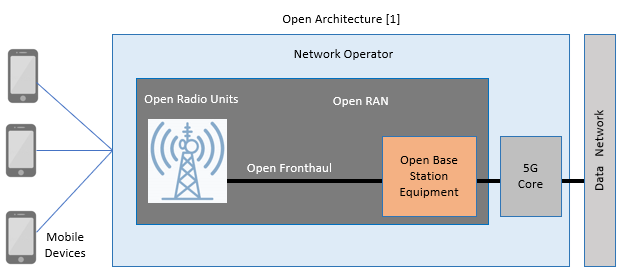
Business advantages of Open RAN
By leveraging open standards and interoperability, Open RAN enables newcomers and smaller players to enter the market and compete with established vendors, which can drive innovation and lower prices for consumers. The main advantages of Open RAN are supplier diversity, lower total cost (including CapEx and OpEx), fostering innovation through market competition, automation, improved performance, and creating new revenue opportunities. Because Open RAN uses open, standardized interfaces and protocols, it is possible to mix and match hardware and software components from different vendors, enabling network operators to customize their networks to meet their specific needs and requirements. This can lead to cost savings, as operators are not tied to a single vendor and can shop around for the best prices and terms. The following diagram created by the O-RAN Alliance summarizes Open RAN benefits.
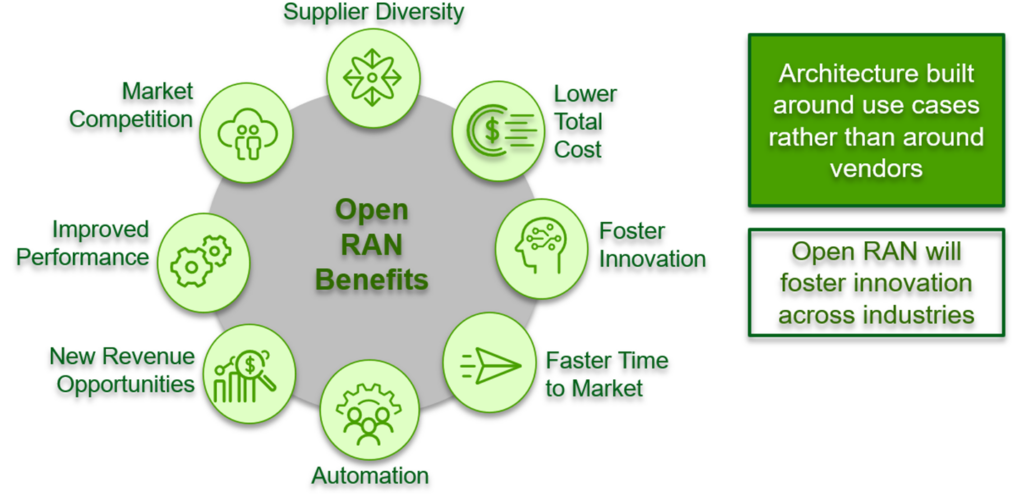
Security of Open RAN
One of the main benefits of Open RAN is that it allows for greater flexibility and innovation in the design and deployment of Radio Access Networks. Open RAN uses open, standardized interfaces and protocols, which makes them more transparent and easier to audit and secure compared to proprietary networks. This can help reduce the risk of vulnerabilities and attacks, as it is easier for security researchers and network operators to identify and fix any issues that may arise. The transparency of Open RAN also allows for easier understanding and auditing to identify and address security vulnerabilities. Additionally, a diverse supply chain in Open RAN networks reduces the risk of a single point of failure compared to Closed RAN networks. Cloudification can improve patching and updating, which can help mitigate security vulnerabilities. Improved interoperability in Open RAN networks also reduces the number of interfaces that need to be secured. Below is a list of the pros and cons of Open RAN versus Closed RAN networks:
Pros of Open RAN
- Greater flexibility and innovation in network design and deployment
- Transparent and easier to audit, plus secure due to use of open, standardized interfaces and protocols
- Reduced risk of vulnerabilities and attacks due to easier identification and fixing of issues
- Open interfaces ensure use and interoperability of secure protocols and security features
- Diverse supply chain reduces risk of a single point of failure – disaggregation enables supply chain security through diversity
- Cloudification can improve patching and updating to mitigate security vulnerabilities
- Improved interoperability reduces the number of interfaces that need to be secured
- Increased visibility enables enhanced intelligence leveraging Artificial Intelligence (AI) and Machine Learning (ML)
- Cloudifications and virtualization
Cons of Open RAN
- May require a larger upfront investment in building and implementing the network
- Requires a certain level of technical expertise to set up and maintain the network
- May not be fully compatible with all existing hardware and software
Pros of Closed RAN
- May have a shorter implementation time and lower upfront costs
- May offer a wider range of hardware and software options
Cons of Closed RAN
- Limited flexibility and innovation in network design and deployment
- Less transparency and more difficult to audit and secure due to use of proprietary interfaces and protocols
- Increased risk of vulnerabilities and attacks due to limited visibility and difficulty in identifying and fixing issues compared to more eyes on Open RAN systems
- Single vendor reliance creates risk of a single point of failure
- May have slower patching and updating processes, leading to increased security vulnerabilities
- Limited interoperability may require securing a larger number of interfaces
If the vendor of a Closed RAN system has a security vulnerability in their hardware or software, it could potentially impact the entire RAN. This risk may be higher in Closed RAN systems compared to Open RAN systems, which use multiple vendors and technologies.
Open RAN security misconceptions
Those vendors who are enjoying the market control of a Closed RAN network mischaracterize the Open RAN security as being overly complex due to the disaggregation of Open RAN systems that may automatically make them less secure compared to traditional network architectures. This is a misconception. Though it is true that the risk of an attack surface may increase due to the disaggregated nature of Open RAN, it is worth noting that the increased complexity of Open RAN architecture does not necessarily make them less secure than traditional network architectures. To establish a secure network, it is common sense to avoid relying solely on a single vendor’s products and solutions to avoid a single point of failure. Open disaggregation nature allows the selection of diverse, independently tested components and can promote competition and innovation within the industry. In fact, the diverse supply chain can help to mitigate the risk of relying on a single vendor and can increase the overall security of the network.
The O-RAN Alliance
The Open Radio Access Network (O-RAN) Alliance is a global organization that promotes and advances the development and deployment of Open RAN technologies. It was founded in February 2018 by AT&T, China Mobile, Deutsche Telekom, NTT DOCOMO, and Orange. The O-RAN Alliance was established as a German entity in August 2018 and its mission is outlined on the O-RAN Alliance website as “to reshape the RAN industry towards more intelligent, open, virtualized, and fully interoperable mobile networks.” O-RAN specifications enable a more competitive and vibrant RAN supplier ecosystem with faster innovations to improve user experience. O-RAN-based mobile networks improve the efficiency of RAN deployments and operations by mobile operators.
The O-RAN Alliance works to develop open standards, interoperability standards, and guidelines for Open RAN, and serves as a forum for industry stakeholders to collaborate so they can share knowledge and experiences. The Alliance closely collaborates with the 3rd Generation Partnership Project (3GPP), a global organization that develops technical standards for telecommunication networks. To ensure that Open RAN technologies are aligned with 3GPP standards and can be seamlessly integrated into existing networks, the O-RAN Alliance has established a security working group that includes members like Fujitsu. This group is responsible for developing security specifications. In the diagram below by the O-RAN Alliance, you can see the architecture includes these security specifications.
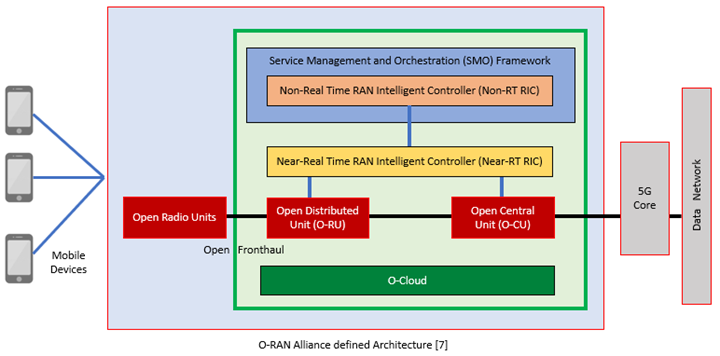
When it comes to security, the O-RAN Alliance has developed a comprehensive threat model for Open RAN networks. This model outlines the various threats and risks that can impact an Open RAN network and provides guidance on how to mitigate and manage these risks. The O-RAN Alliance also emphasizes the importance of secure development and deployment practices, as well as ongoing security monitoring and life cycle management.
Open RAN threat model
The Open RAN security threat model refers to the potential risks and vulnerabilities that may exist in an Open RAN network. These threats can come from various sources, including external hackers, script kiddies, hacktivists, cyber-terrorists, nation-state, malicious insiders, and accidental or intentional system failures. Some examples of security threats that may be relevant to Open RAN include:
- Network attacks: These are attempts to compromise the integrity, availability, or confidentiality of the network or its components. This can include denial of service attacks, man-in-the-middle attacks, and unauthorized access to network resources.
- Data breaches: These occur when sensitive data is accessed or stolen by unauthorized individuals. This can include personal data, financial data, or confidential business information.
- Physical attacks: These are attacks involve physical tampering with network components or infrastructure.
- Software vulnerabilities: These are weaknesses in software that can be exploited by attackers to gain access to the system or steal data.
- Insider threats: These are threats that come from within the organization, such as employees or contractors who have access to the network and may intentionally or unintentionally compromise its security.
Exploiting insecure design, exploiting misconfigurations, jamming the airlink signal through IoT devices, compromising the integrity and availability of log files, exploiting weak authentication and access control are also threats to Open RAN networks.
The O-RAN Alliance security working group has done an excellent job of analyzing these threats and recommending appropriate security controls based on their risk level. While the specific security controls are well documented in O-RAN Alliance security documentation, it is important to note that these controls are not unique to Open RAN systems but can be relevant to any system. To effectively address these security threats, it is necessary to follow a holistic and comprehensive security strategy that includes additional security controls based on industry best practices. By continuously collaborating with ecosystem partners, it is possible to develop the best security and privacy strategies based on the individual regulatory and market context. The following diagram from the O-RAN Alliance shows the different threat agents against O-RAN systems.

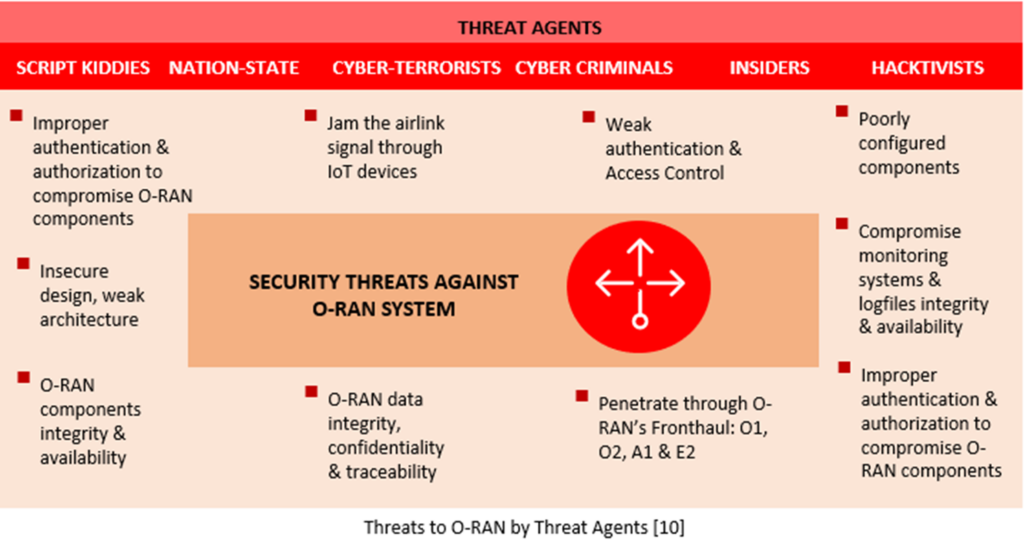
The best approach to Open RAN security
A comprehensive approach to cybersecurity involves considering all aspects of digital security in the enterprise and protecting against all potential vulnerabilities. This includes not only technical measures, such as firewall protection and secure coding practices, but also non-technical measures such as employee training and incident response planning. By considering all potential vulnerabilities and taking a comprehensive approach to security, organizations can better protect themselves from cyber threats. One such comprehensive security framework is coming from the National Institute of Standards and Technology (NIST). The NIST is a non-regulatory agency of the U.S. Department of Commerce that provides technical guidance and standards for a wide range of industries, including information security. The NIST Cybersecurity Framework (CSF) is a widely used set of guidelines and best practices for managing cybersecurity risks in organizations. The framework provides a common language and a structured approach for organizations to assess their current cybersecurity posture, identify and prioritize actions to improve their security, and measure the effectiveness of their security efforts. The NIST CSF is designed to be flexible and adaptable to the specific needs of an organization and can be used by organizations of all sizes and in all sectors. The O-RAN Alliance security recommendations can be combined with the NIST framework while aligning with required industry specific security standards, local and regional level required privacy/security standards and regulations. The following diagram from Pager Duty DevSecOps summarizes the Secure Development Life Cycle.
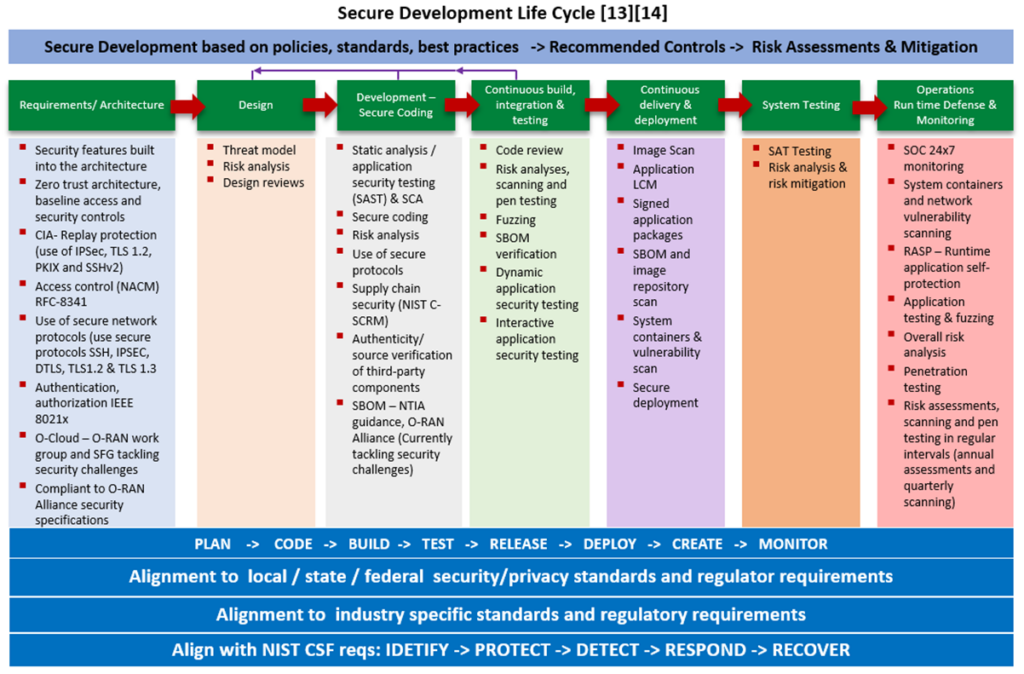
Overall, Open RAN cybersecurity is very important. As telecommunications networks have become increasingly important and critical to our daily lives, it is essential that they are secure and reliable. By adopting open, standardized, and interoperable technologies, Open RAN can help to ensure that telecommunications networks are secure and resilient in the face of evolving threats and challenges.